Email: [email protected] Ligue agora! +55-11-3717-5537
Today’s most sophisticated cybercriminals are increasingly bypassing traditional antimalware solutions and inserting advanced persistent threats deep within networks. These highly targeted attacks evade established signature-based detection by masking their malicious nature in many ways — compression, encryption, polymorphism, the list of techniques goes on.
Some have even begun to evade virtual “sandbox” environments using VM detection, “time bombs” and more. Fighting today’s attacks requires a comprehensive and integrated approach — more than antimalware. More than a virtual sandbox. More than a separate monitoring system.
FortiSandbox offers a robust combination of proactive detection and mitigation, actionable threat insight and integrated and automated deployment. At its foundation is a unique, duallevel sandbox which is complemented by Fortinet’s award-winning antimalware and optional integrated FortiGuard threat intelligence. Years of Fortinet threat expertise is now packaged up and available on site or in the cloud via FortiSandbox.
Suspicious codes are subjected to multi-layer pre-filters prior to execution in the virtual OS for detailed behavioral analysis. The highly effective pre-filters include a screen by our AV engine, queries to cloud-based threat databases and OS-independent simulation with a code emulator, followed by execution in the full virtual runtime environment. Once a malicious code is detected, granular ratings along with key threat intelligence is available, a signature is dynamically created for distribution to integrated products and full threat information is optionally shared with FortiGuard Labs for the update of global threat databases.
All classifications — malicious and high/medium/low risk — are presented within an intuitive dashboard. Full threat information from the virtual execution — including system activity, exploit efforts, web traffic, subsequent downloads, communication attempts and more — is available in rich logs and reports.
The most effective defense against advanced targeted attacks is founded on a cohesive and extensible protection framework. The Fortinet framework uses security intelligence across an integrated solution of traditional and advanced security tools for network, application and endpoint security, and threat detection to deliver actionable, continuously improving protection.
Fortinet integrates the intelligence of FortiGuard Labs into FortiGate next generation firewalls, FortiMail secure email gateways, FortClient endpoint security, FortiSandbox advanced threat detection, and other security products to continually optimize and improve the level of security delivered to organizations with a Fortinet solution.
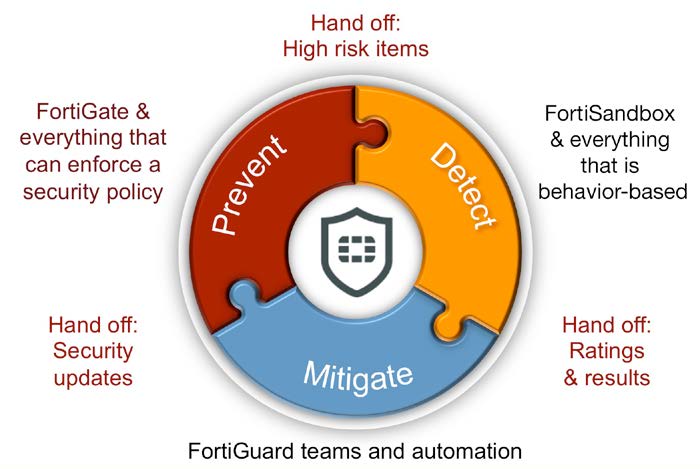
Fortinet next generation firewalls, secure email gateways, web application firewalls, endpoint security and similar solutions use security such as antivirus, web filtering, IPS, and other traditional security techniques to quickly and efficiently prevent known threats from impacting an organization.
FortiSandbox and other advanced detection techniques step in to detect “Zero-day” threats and sophisticated attacks, delivering risk ratings and attack details necessary for remediation.
In a Fortinet solution, detection findings can be used to trigger prevention actions to ensure the safety of resources and data until remediation is in place. Finally, the entire security ecosystem updates to mitigate any impact from future attacks through the strong, integrated threat intelligence research and services of FortiGuard Labs.
Complement your established defenses with a two-step sandboxing approach. Suspicious and at-risk files are subjected to the first stage of analysis with Fortinet’s awardwinning AV engine, FortiGuard global intelligence query*, and code emulation. Second stage analysis is done in a contained environment to uncover the full attack lifecycle using system activity and callback detection. Figure 1 depicts new threats discovered in real time.
In addition to supporting FortiGate, FortiMail, FortiWeb, FortiADC, FortiProxy, FortiClient (ATP agent) and Fabric-Ready Partner submission, third-party security vendor offerings are supported through a well-defined open API set.
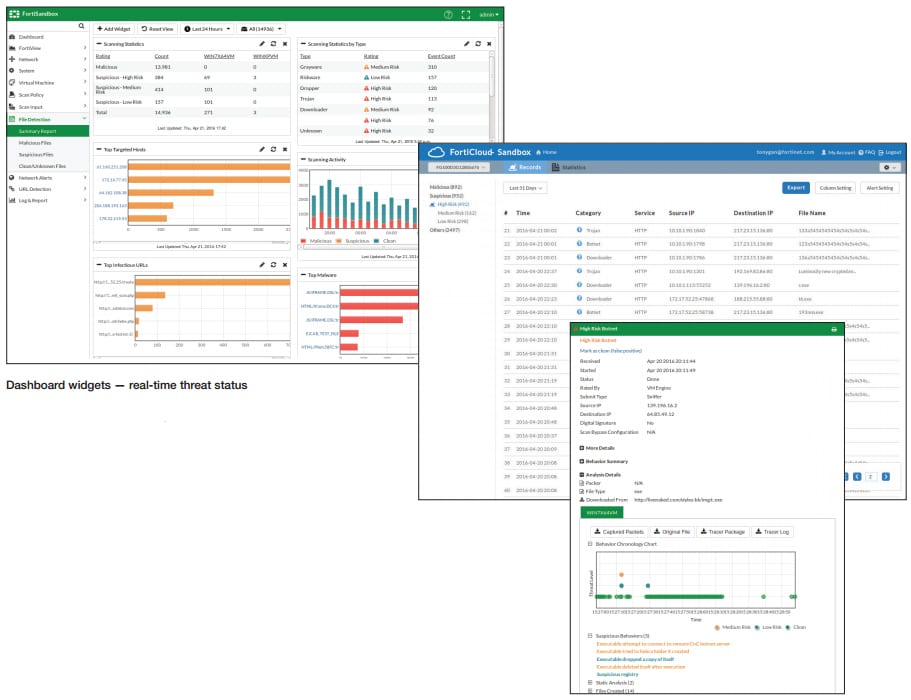
Reports with captured packets, original file, tracer log, and screenshot provide rich threat intelligence and actionable insight after files are examined. This is to speed up remediation.
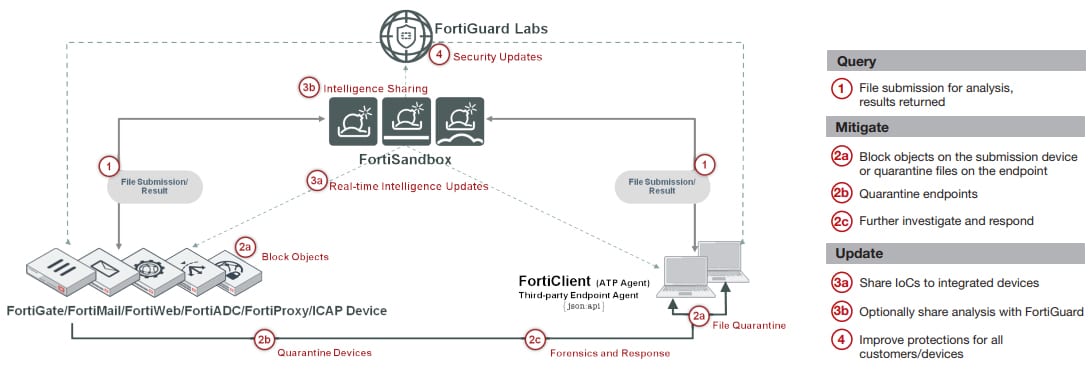
Fortinet’s ability to uniquely integrate various products with FortiSandbox through the Security Fabric offers automatic protection with incredibly simple setup. Once a malicious code is identified, the FortiSandbox will return risk ratings and the local intelligence is shared in real time with Fortinet and third-party vendor-registered devices and clients to remediate and immunize against new advanced threats. The local intelligence can optionally be shared with Fortinet threat research team, FortiGuard Labs, to help protect organizations globally. Figure 3 steps through the flow on the automated mitigation process.
Administration
Networking/Deployment
Systems Integration
Advanced Threat Protection
Monitoring and Report
* a real time IoC check for emerging threats (known good and bad) within the FortiGuard intelligence community
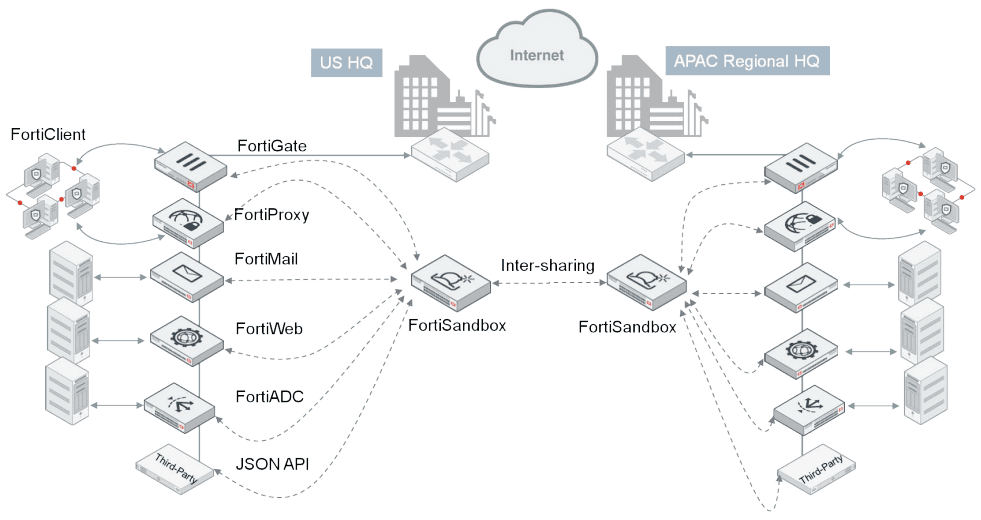
FortiSandbox supports inspection of many protocols in one unified solution, thus simplifies network infrastructure and operations. Further, it integrates within the Security Fabric adding a layer of advanced threat protection to your existing security architecture.
The FortiSandbox is the most flexible threat analysis appliance in the market as it offers various deployment options for customers’ unique configurations and requirements. Organizations can choose to combine these deployment options.
This FortiSandbox deployment mode accepts inputs as an ICAP server or from spanned switch ports or network taps. It may also include administrators’ on-demand file uploads or scanning of file respositories via CIFs or NFS through the GUI. It is the ideal option to enhancing an existing multi-vendor threat protection approach.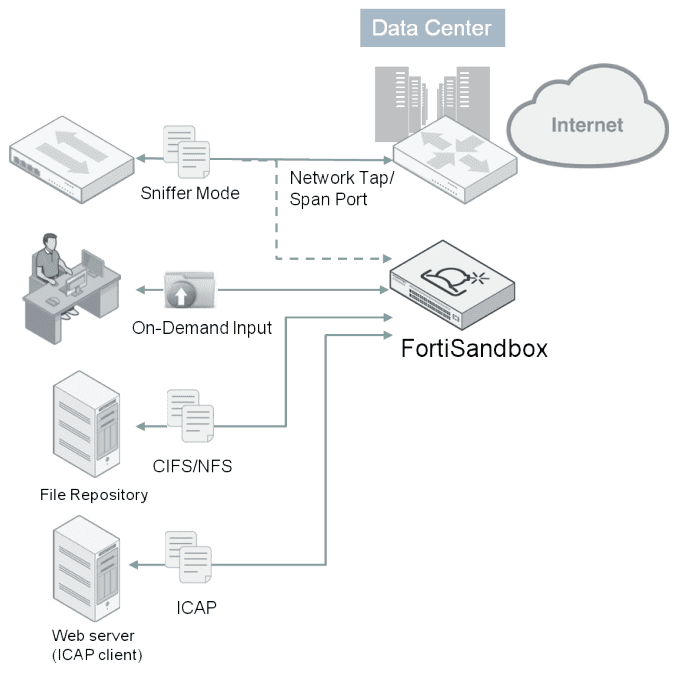
Fortinet products, such as FortiGate, FortiMail, FortiWeb, FortiADC, FortiProxy and FortiClient (ATP agent) and third-party security vendors can intercept and submit suspicious content to FortiSandbox when they are configured to interact with FortiSandbox. The integration will also provide timely remediation and reporting capabilities to those devices.
This integration extends to other FortiSandboxes to allow instantaneous sharing of real-time intelligence. This benefits large enterprises that deploy multiple FortiSandboxes in different geo-locations. This zero-touch automated model is ideal for holistic Figure 4: Standalone Deployment protection across different borders and time zones.
| FortiSandbox VM | |
|---|---|
| Hardware Requirementy | |
| Hypervisor Support | VMware ESXi version 5.1 or later, Citrix XenServer 6.2 or later, Linux KVM CentOS 7.2 or later |
| Virtual CPUs (Minimum / Maximum) | 4 / Unlimited (Fortinet recommends that the number of vCPUs match the number of Windows VM +4.) |
| Memory Support (Minimum / Maximum) | 8 GB / Unlimited |
| Virtual Storage (Minimum / Maximum) | 30 GB / 16 TB |
| Total Virtual Network Interfaces (Minimum) | 6 |
| System | |
| VM Sandboxing (Files/Hour) | Hardware Dependent |
| AV Scanning (Files/Hour) | Hardware Dependent |
| Number of VMs | 4 to 54 (Upgrade via appropriate licenses) |
| FortiGate | FortiClient | FortiMail | FortiWeb | ||
|---|---|---|---|---|---|
| FSA Appliance and VM | File Submission | *FortiOS V5.0.4+ | FortiClient for Windows OS V5.4+ | FortiMail OS V5.1+ | FortiWeb OS V5.4+ |
| File Status Feedback | *FortiOS V5.0.4+ | FortiClient for Windows OS V5.4+ | FortiMail OS V5.1+ | FortiWeb OS V5.4+ | |
| File Detailed Report | *FortiOS V5.4+ | FortiClient for Windows OS V5.4+ | FortiMail OS V5.1+ | – | |
| Dynamic Threat DB Update | *FortiOS V5.4+ | FortiClient for Windows OS V5.4+ | FortiMail OS V5.3+ | FortiWeb OS V5.4+ | |
| FortiSandbox Cloud | File Submission | *FortiOS V5.2.3+ | – | FortiMail OS V5.3+ | FortiWeb OS 5.5.3+ |
| File Status Feedback | *FortiOS V5.2.3+ | – | FortiMail OS V5.3+ | FortiWeb OS 5.5.3+ | |
| File Detailed Report | *FortiOS V5.2.3+ | – | – | – | |
| Dynamic Threat DB Update | *FortiOS V5.4+ | – | FortiMail OS V5.3+ | FortiWeb OS 5.5.3+ |
*some models may require CLI configuration