Email: [email protected] Ligue agora! +55-11-3717-5537
Produto fora de linha
FortiDeceptor is designed to deceive, expose and eliminate advanced attacks by breaking the kill chain and stopping malware from spreading and provide visibility to malicious activity that may have slipped past traditional security controls. It automates the creation of decoys Deception VMs or decoys to provide an internal layer of protection to lure and expose stop attackers that have penetrated the network.
Fortinet Security Fabric provides unified, end-to-end protection with Fortinet Enterprise Firewalls to battle advanced persistent threats. Adding FortiDeceptor as Breach Prevention suite expands your defenses with deception based detection and robust security alert information that is both actionable and automated. FortiDeceptor lays out a layer of Decoys and lures, helping you conceal your valuable network assets behind a fabricated Deception Surface to confuse and redirect attackers while revealing their presence on your network.
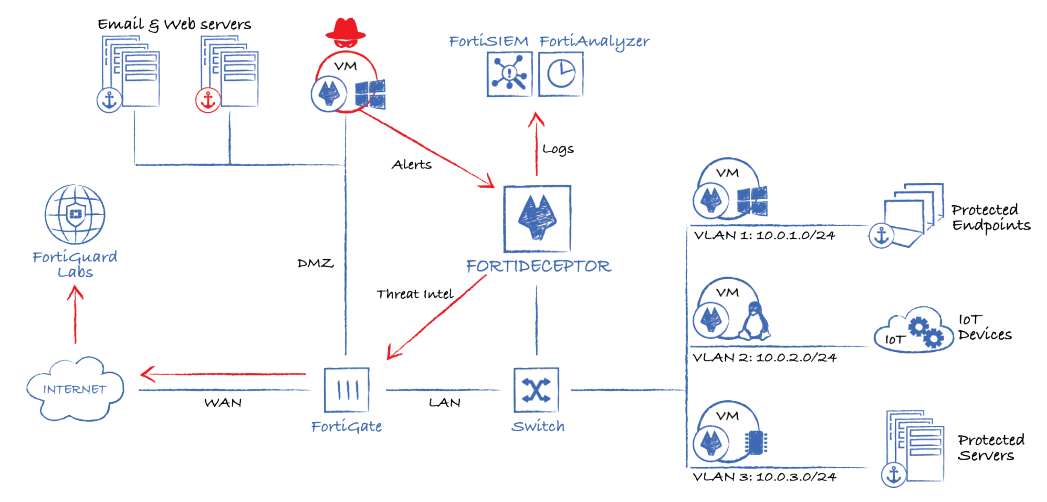
Deploy Decoy VMs and Setup Lures in both Enterprise and SCADA networks to lure hackers to engage with decoy VMs.
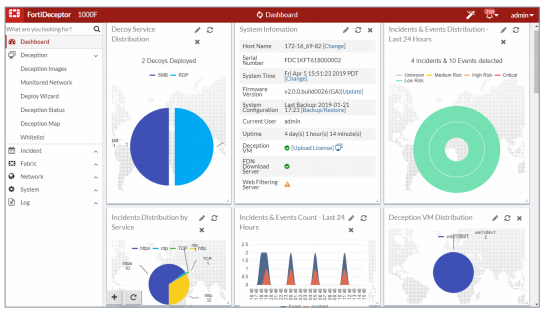
Monitor and correlate incidents and campaigns with information about logins/logouts to hosts, tracking lateral movements, file added/modified/ deleted on Decoy VMs.
Eliminate Attacks to/from Decoys by identifying intrusions, websites visits and malware planted during attacks.
Security Fabric Integration with FortiGate by automated quarantine source of attack.
Generate Custom and Comprehensive Reports from incident tables from the GUI in PDF format.
Configure Alerts and send Alert Notifications via email, SNMP TRAPs, Comment Event Format and SYSLOG.
Deceive external and internal threats with deceptive VM instances and decoys, managed from a centralized location. Deploy a Deception Surface of real Windows, Linux and SCADA VMs that are indistinguishable from real assets, to lure attackers into revealing themselves.
Expose hacker activity with early and accurate detection and actionable alerts. Trace and correlate hacker’s lateral movement and notify Security Administrators through Web UI, Email, SNMP traps and logs. Analyze detailed forensic information of hacker’s lateral movements and activities. Correlate incident and campaign information of attackers’ traffic.
Eliminate threats by redirecting attackers to deception hosts from production servers. Quarantine attackers with FortiGates in Fortinet Security Fabric to and stop connections to C&C servers to break the kill chain. Stop intrusions and malware infection on network.
FortiDeceptor deploys Decoys VMs which inspect the behavior of the attacker and validate the malicious intent. Attackers are redirected to deception hosts and away from customers’ real production servers, thus protecting high value company assets. When an attack has been detected, actionable intelligence (IoCs & TTPs) are subsequently generated and the information is shared across a broad set of in-line security controls through the integration with Fortinet’s Security Fabric to proactively block these unknown threats in real-time. Companies can create automated response processes to shut down current attacks and to prevent or detect future attacks. Security operations teams are notified with alerts and counter intelligence so that the kill chain is broken and attacks can be shut down immediately.
| FORTIDECEPTOR VM | |
|---|---|
| Capacity | |
| Deception VM OS | Windows and Ubuntu |
| VM Instance support | Combination of Windows 7, Windows 10, Linux and/or SCADA |
| VLANs support (maximum) | 32 |
| Deception VMs Shipped | 0 Upgradable to max. 256/td> |
| Virtual Machine | |
| Hypervisor Support | VMWare vSphere ESXi 5.1, 5.5 or 6.0 and later, KVM |
| Virtual CPUs (min / max) | 4 / Unlimited* Intel Virtualization Technology (VT-x/EPT) or AMD Virtualization (AMD-V/RVI). |
| Virtual Network Interfaces | 6 |
| Virtual Memory (min / max) | 4GB / Unlimited** |
| Virtual Storage (min / max) | 200GB / 16TB*** |
* Fortinet recommends that the number of virtual CPUs is one plus the number of VM instance.
** Fortinet recommends that the size of virtual memory is 4GB plus 2 GB for every VM instance.
*** Fortinet recommends that the size of virtual storage is 1TB for production environment.* Fortinet recommends that the number of virtual CPUs is one plus the number of VM instance. ** Fortinet recommends that the size of virtual memory is 4GB plus 2 GB for every VM instance. *** Fortinet recommends that the size of virtual storage is 1TB for production environment.