Email: [email protected] Ligue agora! +55-11-3717-5537
Fortinet’s Browser Isolation platform, FortiIsolator, provides a next level of Advanced Threat Protection (ATP) that integrates with Fortinet’s Security Fabric. It addresses the need to access shared links and web content for business purposes while maintaining the most robust internet hygiene. Specifically, FortiIsolator allows web content to be accessed without the risk of user compromise by maintaining an “air-gap” between the user’s browser and the web content.

Allow user access to potentially malicious content while maintaining strict security
Native integration methods allow the use of standard browsers to access potentially malicious web content without the risk of compromising the user’s desktop – preventing zero-day infections.

Broad Coverage of the Attack Surface with Security Fabric
Integrated with FortiGate and FortiMail for defense against advanced targeted attacks across network, application layers and endpoint devices.
FortiIsolator is a clientless browser isolation solution which allows the user to access potentially malicious content using their regular browser without the risk of compromising their browser, desktop or mobile device. FortiIsolator is designed to work as unobtrusively as possible, interoperating with any modern HTML5 capable browser (ie: Edge, Chrome, Safari, Firefox), meaning no requirement for any client or plugin software on the end user device.
FortiIsolator prevents drive-by and watering hole attacks by accessing the potentially malicious content in a trusted execution container which is disposed of at the end of the browser session and presenting the user with a visual rendering of the web page. This rendered version of the web page can still be interacted with e.g. videos viewed, links clicked, and PDF files opened. However, the rendering process prevents any content from being able to cross over to the user’s system.
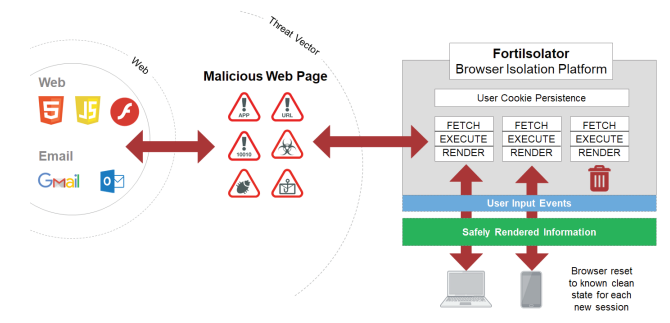
Email is the most common attack vector for malware (92.4%) and social attacks such as phishing (96%) and the majority of that is delivered via web links. Steps can be taken to filter known malicious and unrated links, however, the latter may impact productivity. By combining FortiIsolator with your Secure Mail Gateway, Firewall, Secure Web Gateway or Desktop Client, you are able to allow users to access URLs while maintaining security — increasing productivity.
| FORTIISOLATOR 1000F | |
|---|---|
| Hardware Specifications | |
| 10/100/1000 Interfaces (Copper, RJ45) | 4 |
| Storage | 1x 1 TB |
| Form Factor | 1RU |
| Power Supply | Single (Dual Optional) |
| System Specifications | |
| Concurrent Browser Sessions | 250* |
| Supported Browsers | Chrome, Firefox, Microsoft Edge, Microsoft Internet Explorer, Safari, Opera |
| Integration Methods | Proxy, URL Rewrite, Transparent Inline |
| Performance (Messages/Hour) [Without queuing based on 100 KB message size] | |
| Concurrent Browser Sessions | 250 |
| Dimensions | |
| Height x Width x Length (inches) | 1.73 x 17.24 x 22.83 |
| Height x Width x Length (mm) | 44 x 438 x 580 |
| Weight | 25 lbs (11.4 kg) |
| Environment | |
| Power Source | 100–240V AC, 50–60 Hz |
| Maximum Current | 110V/5.0A, 220V/3.0A |
| Maximum Power Required | 117 W |
| Power Consumption (Average) | 67 W |
| Heat Dissipation | 398 BTU/h |
| Humidity | 5–90% non-condensing |
| Operating Temperature | 32–104°F (0–40°C) |
| Storage Temperature | -40–158°F (-40–70°C) |
| Compliance | |
| FCC Part 15 Class A, C-Tick, VCCI, CE, UL/cUL, CB, BSMI, RoHS | |
| #FIS-1000F | FortiIsolator 1000F Appliance. Supports up to 250 Concurrent Web Sessions. | |||||
| #FC-10-1000F-623-02-12 | 1 Ano – FortiIsolator-1000F 1 Year Web Isolation Bundle – Includes 24×7 FortiCare support, Web Isolation and FortiGuard Security Services for 250 concurrent sessions . | |||||
| #FC-10-1000F-623-02-36 | 3 Anos – FortiIsolator-1000F 3 Year Web Isolation Bundle – Includes 24×7 FortiCare support, Web Isolation and FortiGuard Security Services for 250 concurrent sessions . | |||||
| #FC-10-1000F-623-02-60 | 5 Anos – FortiIsolator-1000F 5 Year Web Isolation Bundle – Includes 24×7 FortiCare support, Web Isolation and FortiGuard Security Services for 250 concurrent sessions . | |||||
| #SP-FSA1000F-PS | AC power supply for FDC-1000F, FIS-1000F, FSA-1000F, module only | |||||